| Source | https://bazaar.abuse.ch/sample/f47af17b82cdd753cbba4f75be9e372ac7dca17452572c57df64f5bfea74abe9/ |
| Analysis Environment | REMnux |
Overview
This Excel document contains malicious macros that are obfuscated to avoid detection. When opened and macros are enabled, it attempts to reach out to external resources hosted on malicious URLs and download and execute additional payloads.
Basic Static Analysis
On Malware Bazaar, the sample was observed to have been submitted on October 11, 2024.
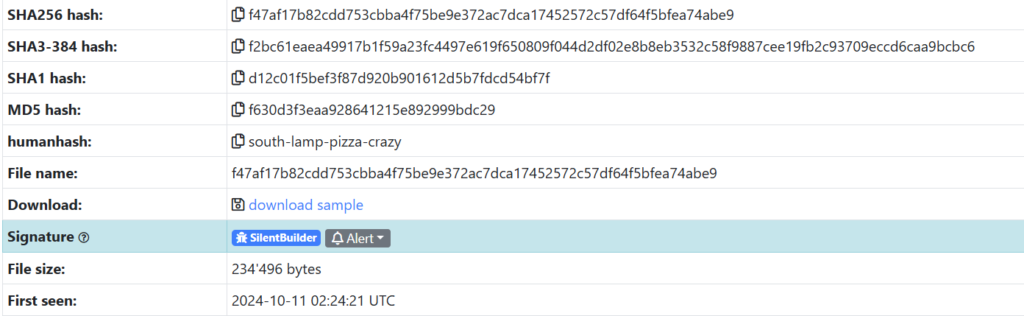
Figure 1:Malware Bazaar page
Submitting the file hash to VirusTotal showed that 41 out of 63 antivirus engines found it suspicious.
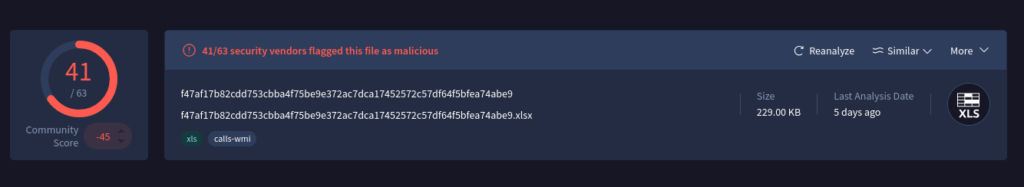
Figure 2: VirusTotal Scan output
The detail section on VirusTotal revealed that the sample was created in 2015 and was first observed in the wild in 2021. Therefore, it is safe to conclude that while the malware was recently uploaded on Malware Bazaar, it has long existed in the wild.
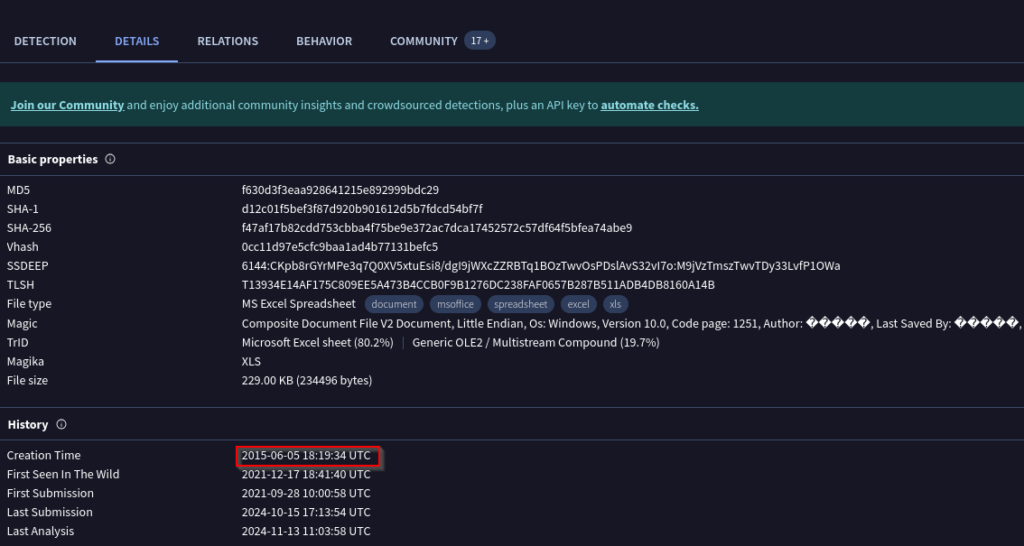
Figure 3: VirusTotal Detail section
Static Macro Analysis
An Excel spreadsheet is like a compressed file. I began the analysis by unzipping the file to see the files it contained.
Figure 4: Unzipping the spreadsheet
Figure 5: Unzipped folder
oledump
Then, I used ole dump to parse the file, revealing the sections or streams of data in it. This revealed 3 sections with varying sizes and names, as shown below.
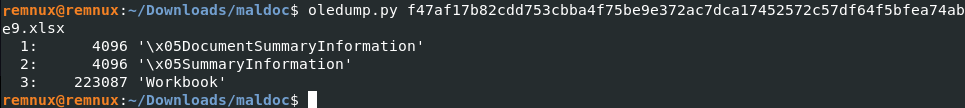
Figure 6: File parsing with oledump
Stream 3 appeared to have the largest size and contained the main data. Hence, I analysed it with the command Oledump.py -s 3 f47af17b82cdd753cbba4f75be9e372ac7dca17452572c57df64f5bfea74abe9.xlsx, which prints out the stream’s hexadecimal data.
The flag -s in the command represents the data stream, and the number ‘3’ is the stream number.
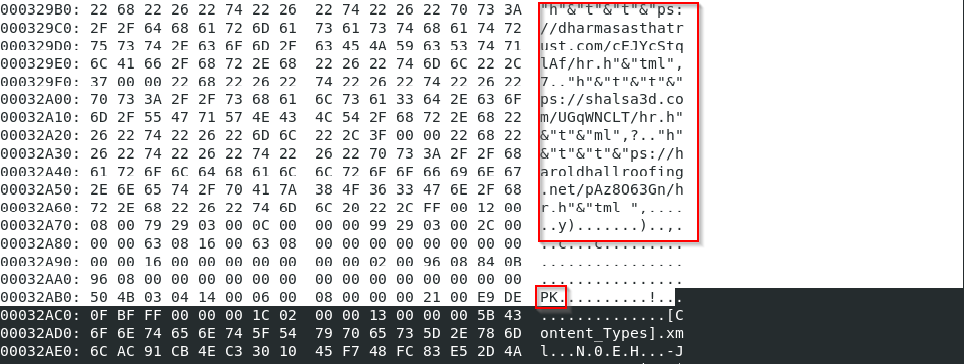
Figure 7: Hexadecimal output of stream 3
The output revealed strings that appear to be URLs and names consistent with those observed when we unzipped the file.
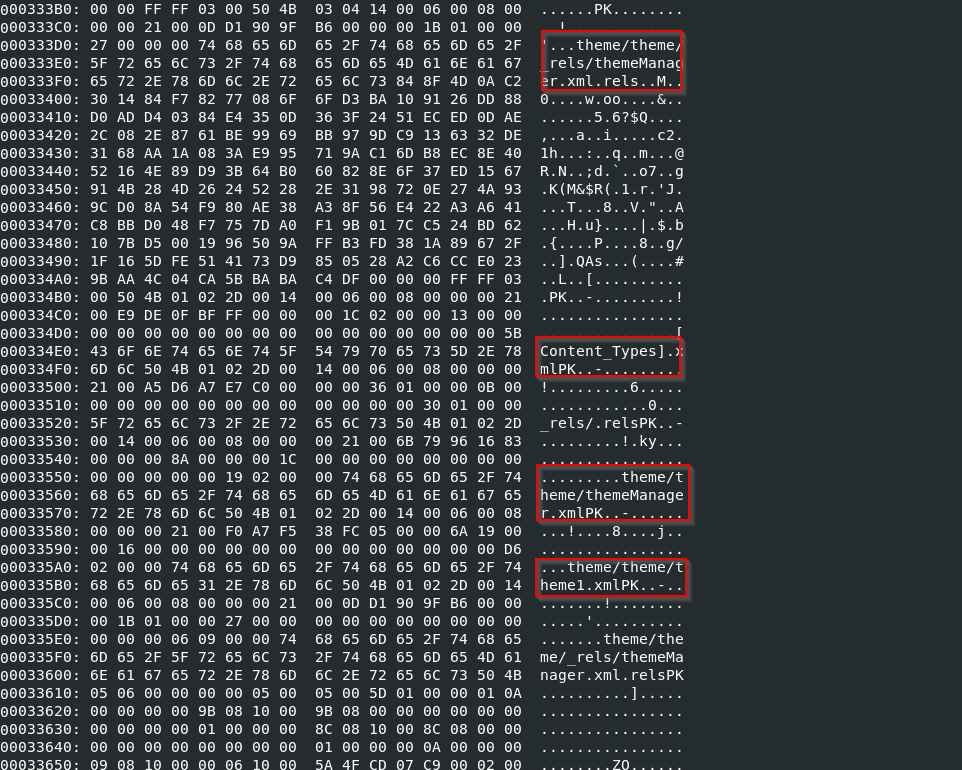
Figure 8: Observed strings in stream 3
To better display the strings found, I ran the last command again, but with a flag of capital S for strings.
$ oledump.py -s 3 -S f47af17b82cdd753cbba4f75be9e372ac7dca17452572c57df64f5bfea74abe9.xlsx
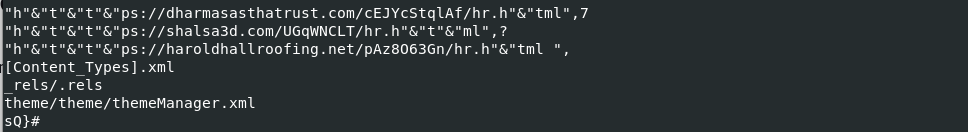
Figure 9: Observed URLs in stream 3
Deobfuscating the URLs revealed 3 potential network indicators of compromise. To avoid accidentally visiting them, they have been defanged with “[ ].”
- https[:]//haroldhallroofing[.]net/pAz8O63Gn/hr.html
- https[:]//shalsa3d.com/UGqWNCLT/hr[.]html
- https[:]//dharmasasthatrust[.]com/cEJYcStqlAf/hr.html
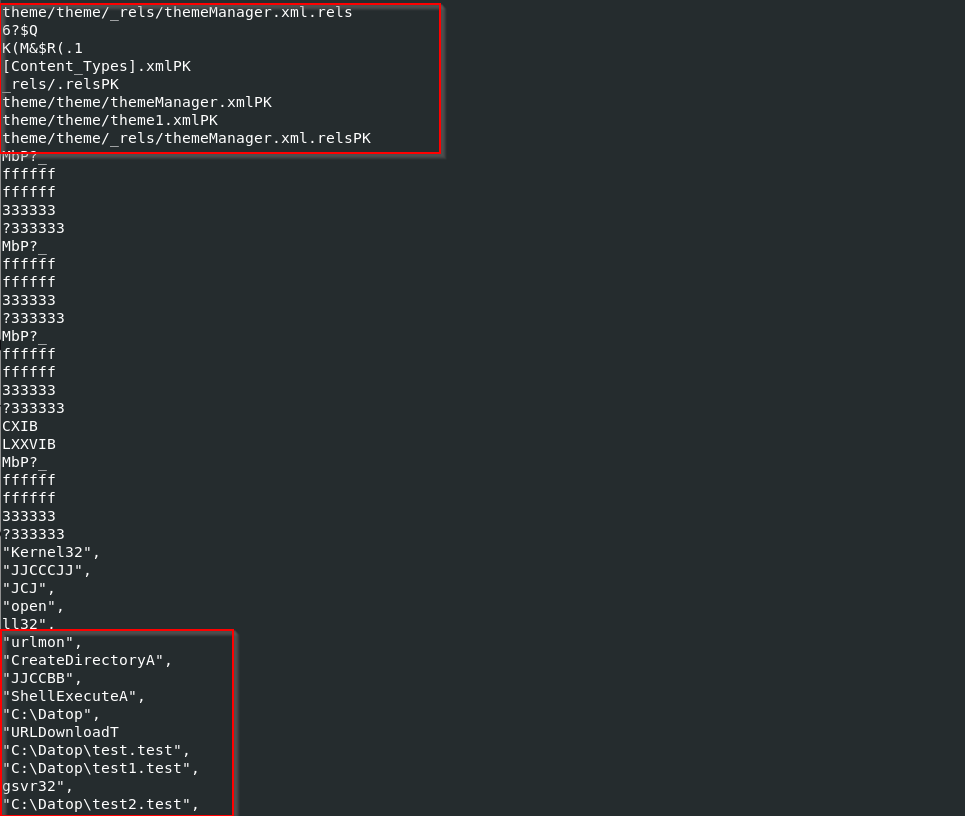
Figure 10: Observed API calls
This time, I found not only the strings from the hexadecimal data representation but additional ones like URLDownloadT, ShellExecuteA and C:\Datop\test2.test.
The presence of the urlmon API call means that the application intends to perform network activities.
The URLMON API (also known as urlmon.dll) is used in Windows operating systems to handle various internet-related tasks. It provides functions and interfaces for applications to interact with URLs, such as opening web pages, downloading files, and handling different internet protocols.
The ShellExecuteA function is part of the Windows API and is used to execute, run or open a file.
The file paths can be assumed to represent the directories where the potentially downloaded files are saved and their names.
olevba
I then used the olevba tool to parse the file, identifying suspicious VBA keywords and auto-executable macros, decoding obfuscated strings, and converting the code into clear text for analysis.
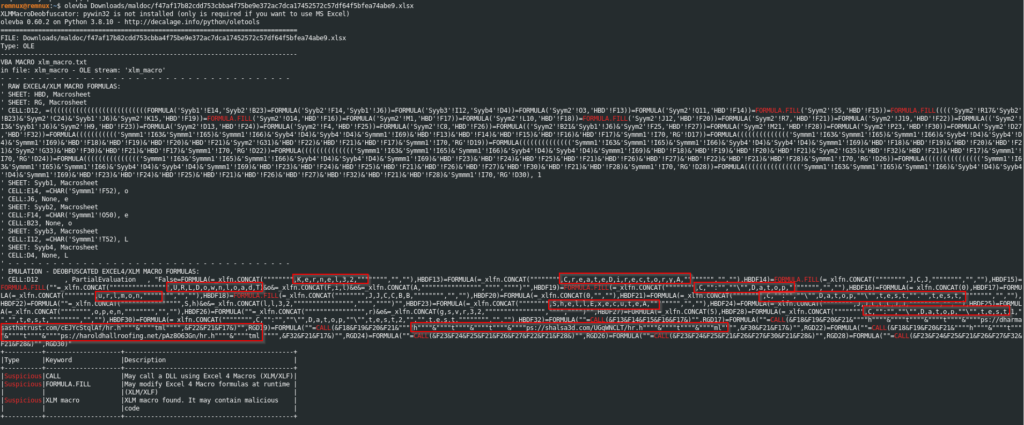
Figure 11: File parsing with olevba
Key Parts:
- XLM MACRO Detection:
- The scan has detected XLM macros. Excel 4.0 (XLM) macros are an older macro format that can still be used to execute malicious payloads.
- Obfuscated XLM Macros:
- The macros contain a series of obfuscated or encoded formulas using functions like FORMULA.FILL and CALL to assemble and execute commands dynamically, at run time.
- The obfuscation uses complex xlfn.CONCAT functions and string manipulation to construct commands and URLs.
- Malicious Indicators:
- The presence of suspicious functions like CALL indicates the potential execution of DLLs or other system functions, which is a common method used by malware to perform malicious actions.
- URLs like https[:]//sastrahurst.com, https[:]//haroldhalroofing[.]net, and others are embedded within the macros, which could be used to download additional payloads or exfiltrate data.
- Strings like “CreateDirectoryA”, “ShellExecuteA”, and “URLDownloadToFile” imply network activity and interaction with the Windows API to download files or execute commands.
Conclusion:
The Excel file contains XLM (Excel 4.0) macros, an older yet viable method for executing malicious payloads. These macros are heavily obfuscated, utilizing complex formulas such as FORMULA.FILL and CALL to dynamically assemble and execute commands at runtime. The obfuscation employs advanced string manipulation, including xlfn.CONCAT functions to construct URLs and system commands covertly.
The use of the CALL function suggests the potential execution of system-level operations, such as running DLLs or interacting with the Windows API. Embedded URLs like https[:]//sastrahurst.com and https[:]//haroldhalroofing[.]net and API-related strings such as “CreateDirectoryA,” “ShellExecuteA,” and “URLDownloadToFile” indicate possible network activity aimed at downloading or executing external files or sensitive data exfiltration.
Yara rule
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 | rule Malicious_XLM_Macro{ meta: description = "Detects malicious Excel 4.0 (XLM) macros with obfuscated code and network activity" author = "SecOpsBro" date = "2024-11-19" reference = "XCEL Macro Analysis Report" strings: $xlfn_CONCAT = "xlfn.CONCAT" ascii $formula_fill = "FORMULA.FILL" ascii $call_function = "CALL" ascii $create_directory = "CreateDirectoryA" ascii $shell_execute = "ShellExecuteA" ascii $url_download = "URLDownloadToFile" ascii $url1 = "https://sastrahurst.com" ascii $url2 = "https://haroldhallroofing.net" ascii $url3 = "https://shalsa3d.com" ascii $url4 = "https://dharmasasthatrust.com" ascii condition: 1 of ($xlfn_CONCAT, $formula_fill, $call_function) and 1 of ($create_directory, $shell_execute, $url_download) and any of ($url1, $url2, $url3, $url4)} |
